If you’ve ever tried connecting to a server via SSH and seen the message “Warning: Remote Host Identification Has Changed”, you’re not alone. This error is a common issue for developers, DevOps engineers, and system administrators. It appears when the SSH client detects that the host key of the remote server no longer matches the one stored in your local `known_hosts` file. While it can be harmless — such as when reconnecting to a cloud instance with a new IP — it may also signal a potential security threat like a man-in-the-middle attack. In this article, we’ll break down why this warning happens and how to fix it. Let’s dive in.

What Is the “Warning: Remote Host Identification Has Changed” Error?
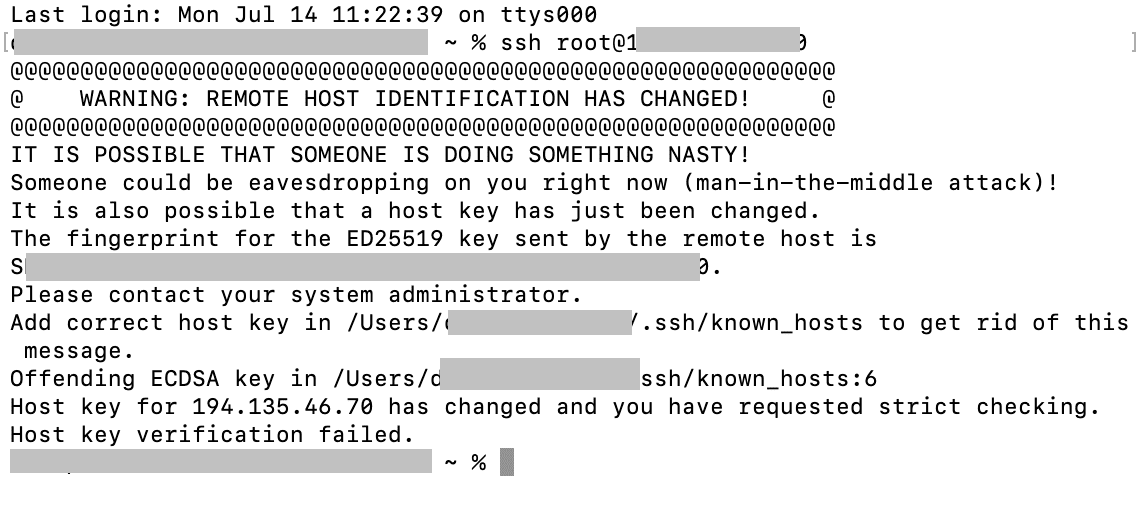
The “Warning: Remote Host Identification Has Changed” is an SSH security feature designed to protect you from connecting to a potentially malicious server. When you first connect to a remote host using SSH, your client stores the server’s unique cryptographic host key in a local file called `known_hosts`. This key acts as a digital fingerprint that identifies the server. On subsequent connections, SSH checks whether the stored key matches the one presented by the server. If there's a mismatch — for example, because the server was reinstalled, migrated, or had its SSH keys regenerated — your SSH client throws this warning to alert you of the discrepancy.
While it might seem like a minor annoyance, this message plays a crucial role in securing your connection. Ignoring it without investigation could expose you to man-in-the-middle (MITM) attacks, where an attacker intercepts your traffic by impersonating the server. So, while the change might be benign, it’s always worth verifying before proceeding.
How the known_hosts File Helps SSH Authentication
The `known_hosts` file is a critical part of SSH’s security model. Located in your local `.ssh` directory (`~/.ssh/known_hosts` on Unix-like systems), it stores cryptographic fingerprints — or host keys — of remote servers you've previously connected to. Each time you initiate an SSH connection, your client checks this file to verify that the server's identity hasn't changed. If the server presents a key that doesn’t match the one stored in `known_hosts`, SSH blocks the connection and displays the “Remote Host Identification Has Changed” warning. This mechanism helps prevent impersonation and man-in-the-middle attacks by ensuring you're connecting to the same trusted server every time. While it's sometimes necessary to update this file — especially with dynamic cloud environments — it should be done carefully to maintain security.
How to Fix the “Warning: Remote Host Identification Has Changed” SSH Error: Step-by-Step Guide
Before proceeding, make sure you’re connecting to the correct server . Confirm the IP address or hostname is what you expect. If you're confident it's safe, here's how to resolve the error:
-
Trigger the Warning (Optional). To see the error firsthand, try connecting to the server:

-
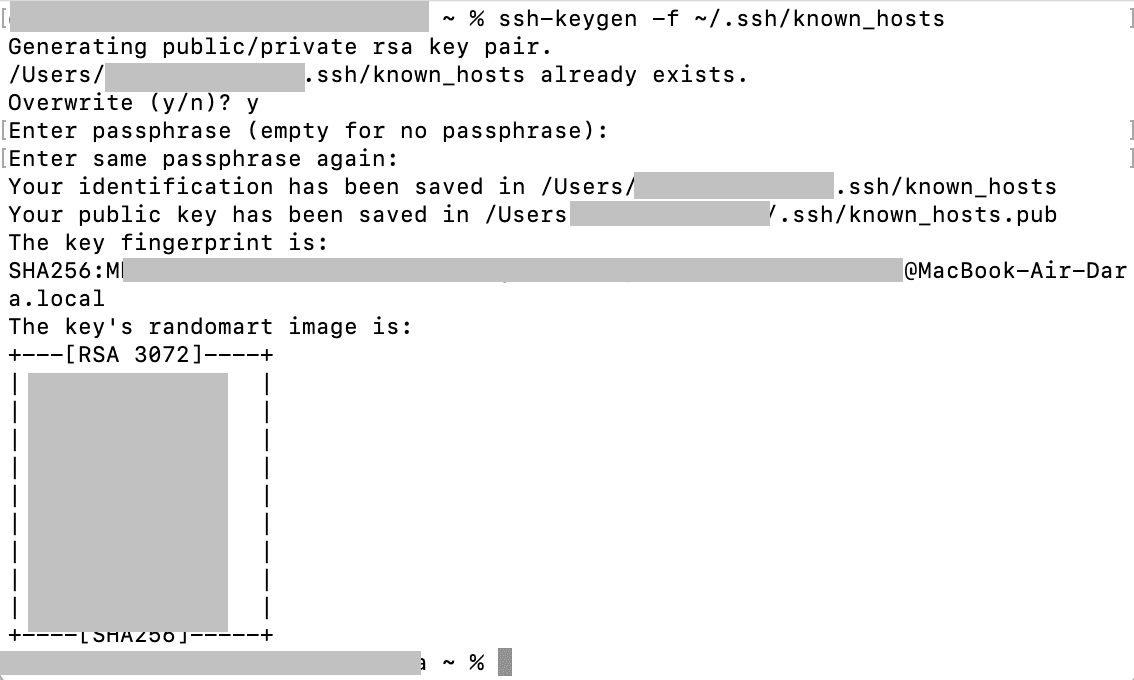
Clear the old fingerprint:
You’ll see:
Type y and press Enter. Next, you’ll be asked:
Just press Enter (no passphrase). Do the same on the next line. You’re not adding security here — you’re resetting a file, not creating a real key. Now reconnect with ssh root@your-server-ip, type yes again, and the new server key will be saved cleanly. Warning gone.

-
On Windows using OpenSSH, the path might look like:
-
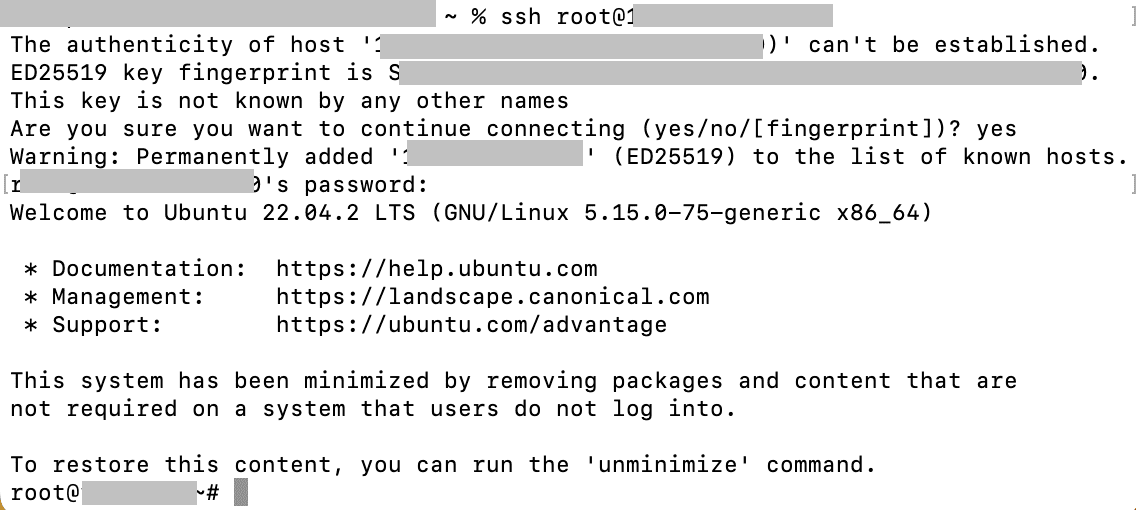
Reconnect to the Server. When reconnecting, the system may ask you if you want to continue. Enter “yes”.

The updated key will be added to your known_hosts file, and the warning should no longer appear.
Best Practices and Security Considerations
While resolving the “Remote Host Identification Has Changed” warning is straightforward, it’s important to approach host key management with care. Never blindly accept or delete keys without verifying the server’s identity — this can expose you to man-in-the-middle attacks. A good practice is to regularly audit your known_hosts file , especially if you work with dynamic environments like cloud instances or containers that frequently change IPs or rebuild SSH keys. In automated workflows such as CI/CD pipelines, consider using tools like ssh-keygen or scripts to manage known hosts programmatically, ensuring both security and reliability.
For teams working across multiple environments, implementing strict SSH policies — such as signed host certificates or integrating SSH key verification into configuration management tools (Ansible, Puppet, etc.) — can help maintain trust without sacrificing convenience. Also, avoid disabling host key checking (e.g., using StrictHostKeyChecking=no) in production or shared environments. While it might seem convenient, doing so undermines one of SSH’s core security features. In short: treat your SSH host keys with the same level of attention as user credentials. Proper host key management is a small effort that pays off significantly in long-term security and operational stability.
Conclusion
The “Remote Host Identification Has Changed” error is a built-in security mechanism in SSH, not a flaw or bug. Ignoring it can expose you to serious risks, including man-in-the-middle attacks. However, with the right knowledge, this issue can be resolved quickly and safely — especially when you're certain the host key change is legitimate. Whether you're managing cloud servers, automating deployments, or simply connecting to a remote machine, understanding how SSH verifies host identities is key to secure usage. The tools and commands provided in this guide give you the power to fix the warning without compromising security.
In the world of SSH troubleshooting, staying secure doesn’t have to come at the cost of convenience. With careful management of known hosts and a clear understanding of your environment, you can maintain both seamless access and strong protection across all your SSH connections.